What Is Access Control System? Learn Its Benefits & Types
- Бонус за регистрацию онлайн казино
- Sep 11, 2025
- 17 min read
Think about the last time you used a key. You put it in the lock, turned it, and the door opened. Simple, right? But that traditional lock and key has some serious limitations. What if someone loses their key? Or you need to give temporary access to a contractor? You’d have to change the locks—a costly and time-consuming hassle.
An access control system is the modern, intelligent answer to that old problem. It's a system that acts as a digital gatekeeper, deciding who gets in, where they can go, and even when they’re allowed to be there. Instead of a metal key, it uses things like key cards, fingerprint scanners, or even your smartphone to grant or deny access based on rules you create.
What Is an Access Control System Really

Let’s go back to the classic lock and key. It’s a binary setup: you either have the key or you don’t. There’s no in-between.
This is where understanding what is an access control system really clicks. It’s not just about opening a door; it’s about managing access with intelligence. Think of it like a smart, highly-trained security guard for your building. The guard doesn't just glance at a ticket. They check your ID to see who you are, consult a list to confirm you’re allowed in that specific area, and make a note of when you came and left.
An access control system does all of that automatically. It moves security from a simple "yes/no" to a nuanced, powerful tool for managing your space.
The Three Pillars of Access Control
Every access control system, no matter how simple or complex, is built on three core ideas. These three pillars work together seamlessly to create a secure and accountable environment.
Authentication: This is the "who are you?" step. The system needs to confirm your identity before doing anything else. It's the moment you present your credential—tapping a key card, entering a PIN, or scanning your fingerprint.
Authorization: Once the system knows who you are, it asks, "What are you allowed to do?" This is where your permissions come in. A manager might have 24/7 access to the entire building, while a new intern can only get into the main office between 9 AM and 5 PM on weekdays.
Auditing: This is the "what happened?" pillar. The system keeps a detailed log of every single access event—both successful entries and failed attempts. This trail is incredibly useful for reviewing security incidents, tracking building usage, or ensuring compliance.
These three functions are what separate a smart access control system from a dumb lock. You gain dynamic, granular control that transforms security from a passive barrier into an active management tool.
To see how these pillars work in practice, let's look at the core functions in a bit more detail.
Core Functions of an Access Control System
The table below breaks down these three essential functions with everyday examples, showing how they form the backbone of any reliable security setup.
Function | Description | Real-World Example |
|---|---|---|
Authentication | Verifying a user's identity to ensure they are who they claim to be. | An employee scans their company-issued ID badge at a door reader. |
Authorization | Granting or denying specific permissions based on pre-defined security policies. | The system checks the employee's role and allows them into the marketing office but denies entry to the finance department after 6 PM. |
Auditing | Recording and logging all access attempts, both successful and failed, for review. | A manager reviews the access logs to confirm which employees were in the building over the weekend during a security incident. |
By building on this foundation of authenticating, authorizing, and auditing, modern systems can offer sophisticated features that keep people and property safe.
How the Core Components Work Together

Think of an access control system like a highly efficient security team, where each member has a specific job. When they all work in perfect sync, you get a robust system that grants or denies access in the blink of an eye.
Imagine you're walking up to a secure office door. The moment you present your key card, you kick off a rapid, four-step conversation between the system’s core parts. This entire process—from tapping your card to the lock clicking open—happens in less than a second.
So, how does it all come together? Let's meet the key players in this security orchestra.
The Credentials: Your Identity Card
First up, you have the credential. This is simply the unique identifier that tells the system who you are. It's the modern, intelligent version of a traditional metal key.
Credentials come in all shapes and sizes, designed to fit different security levels and user preferences. The most common ones you'll see are:
Key Cards and Fobs: The classic plastic cards or small tokens you tap or wave at a reader. They use RFID or NFC to send your ID.
Mobile Credentials: Your smartphone acts as your key. An app on your phone uses Bluetooth or NFC to talk to the reader, making for a super convenient, key-free experience.
Biometrics: This is as personal as it gets. These systems use your unique biological traits—like a fingerprint, facial scan, or even your iris pattern—to confirm it's really you.
PIN Codes: A simple numeric code typed into a keypad. These are often paired with another credential as a second layer of security.
The credential is just the first piece of the puzzle. It holds the "key," but it needs someone to show it to.
The Readers: The Gatekeepers
That's where the reader comes in. This is the device mounted next to the door, and its only job is to "read" the information from your credential. Think of it as the bouncer at the door, checking IDs.
When you tap your card or hold up your phone, the reader grabs your unique identifier and securely passes it up the chain for verification. Some readers are straightforward scanners, while others are more complex, with built-in keypads or biometric sensors. For instance, some systems use specialized input devices like inductive proximity sensors to know when an access card is presented.
Once the reader has your info, it sends it on to the brain of the operation.
The Control Panel: The Brain
The access control panel is the real decision-maker. This piece of hardware is the central nervous system connecting the readers, locks, and software. It takes the credential data from the reader and instantly checks it against the rules you've set.
The panel asks a few crucial questions:
Is this credential even valid?
Does this person have permission for this specific door?
Are they trying to get in during an approved time?
If the answer to all of these questions is a firm "yes," the panel sends a signal to unlock the door. If any answer is "no," access is denied. Simple as that.
The Software: The Command Center
Finally, we have the management software. This is your command center, the dashboard where you set all the security rules that the control panel enforces. From here, you can add or remove users, create different access levels for different groups, and set schedules for when doors can be opened.
This software is where the "control" in access control really comes to life. It’s where you can instantly revoke a lost card, grant temporary access to a visitor, or pull detailed reports of every door entry.
The importance of these systems is reflected in their rapid growth. The global access control market was valued at around USD 12.8 billion in 2025 and is expected to climb past USD 28.41 billion by 2035. Hardware, especially components like biometric scanners, is projected to command about 55.5% of the market, showing a clear shift toward more sophisticated verification methods.
Understanding the Different Types of Access Control
Not every lock needs the same kind of key. You’d use a simple padlock for a garden shed but a complex alarm system for a bank vault, right? The same logic applies to access control. Different environments have different security needs, which is why there are several models for managing who gets in and who stays out.
Think of these models as the "operating system" for your security. They set the ground rules for how permissions are granted and enforced. Picking the right one is critical because it directly impacts how flexible, scalable, and genuinely secure your setup will be.
Let's break down the three main types: Discretionary, Mandatory, and Role-Based.
Discretionary Access Control (DAC)
Imagine you write a report on your computer and need to share it with a colleague. You simply right-click, hit "share," and give them permission to view or edit it. That’s Discretionary Access Control (DAC) in a nutshell.
In a DAC system, the owner of the resource—be it a file, a room, or a piece of equipment—has full discretion over who gets access. It’s a very decentralized and flexible approach, perfect for places where people need to share things easily.
The Gist: The person who creates or owns the asset calls the shots on who can access it.
Simple Analogy: It’s like giving a friend a spare key to your house. You decide who gets one and can ask for it back anytime.
Where it Fits Best: Collaborative settings like small businesses, university departments, or file-sharing platforms where users manage their own data.
The downside? That same flexibility can be a security headache. When everyone is managing their own permissions, it's tough to enforce a consistent security policy across the board. That makes DAC a poor choice for highly sensitive environments.
Mandatory Access Control (MAC)
Now, let's shift gears and think about a top-secret military base. An individual officer doesn't get to decide who can enter a classified area. Instead, access is dictated by a strict, system-wide policy based on security clearance levels. This is the world of Mandatory Access Control (MAC).
With a MAC model, a central authority assigns security labels to everything (e.g., "Confidential," "Top Secret") and clearance levels to every user. The system then acts as the ultimate gatekeeper, enforcing one simple rule: you only get in if your clearance is equal to or higher than the resource's security level.
In a MAC system, users have zero control over permissions, even for things they create themselves. The rules are mandatory and enforced automatically, providing the highest level of security and preventing data leaks.
This model puts security and confidentiality above all else, which is why it’s the standard for government agencies, military operations, and any organization handling incredibly sensitive information.
Role-Based Access Control (RBAC)
Most businesses need something that sits between the freewheeling nature of DAC and the ironclad structure of MAC. That middle ground is where Role-Based Access Control (RBAC) shines, and it's easily the most common model used today.
Picture a large hospital. Doctors, nurses, and administrators all need access to different patient records and physical areas to do their jobs. Instead of creating unique permissions for hundreds of employees, the hospital assigns access rights to roles like "Doctor," "Nurse," or "Administrator."
When a new nurse starts, they're simply assigned the "Nurse" role and instantly get all the permissions they need. If they leave the hospital, an administrator just removes the role, and their access is gone in a flash.
The Gist: Your job title determines what you can access.
Simple Analogy: Think of your job role as a master key that only opens the doors required for your specific duties—no more, no less.
Where it Fits Best: Almost any organization with defined job functions. It simplifies security management, makes it easier to meet compliance rules, and naturally enforces the principle of least privilege.
Choosing the right model is a big decision. To make it a bit clearer, here's a quick comparison of how these three approaches stack up.
Comparison of Access Control Models
A side-by-side look at the primary access control models to clarify their unique approaches to security and management.
Model Type | Who Controls Access | Best Suited For | Common Example |
|---|---|---|---|
Discretionary (DAC) | The owner of the resource | Small, collaborative teams and file-sharing systems | A user sharing a Google Doc with a coworker |
Mandatory (MAC) | A central authority via system-wide policies | Military, government, and high-security environments | Accessing classified documents based on clearance level |
Role-Based (RBAC) | System administrators who assign permissions to job roles | Most businesses, from mid-sized to large enterprises | A bank teller's access to customer accounts |
Each model offers a different balance of flexibility and control. By understanding these core differences, you can better select the framework that truly aligns with your organization's security goals.
It's also important to remember that digital systems are just one part of the equation. Physical security is the first line of defense, and things like robust security fencing are essential for creating a secure perimeter in the first place. The growing importance of comprehensive access control is reflected in the market size, which was valued at around $9.9 billion in 2024 and is projected to hit $10.76 billion in 2025.
The image below highlights just how effective a well-implemented system can be.
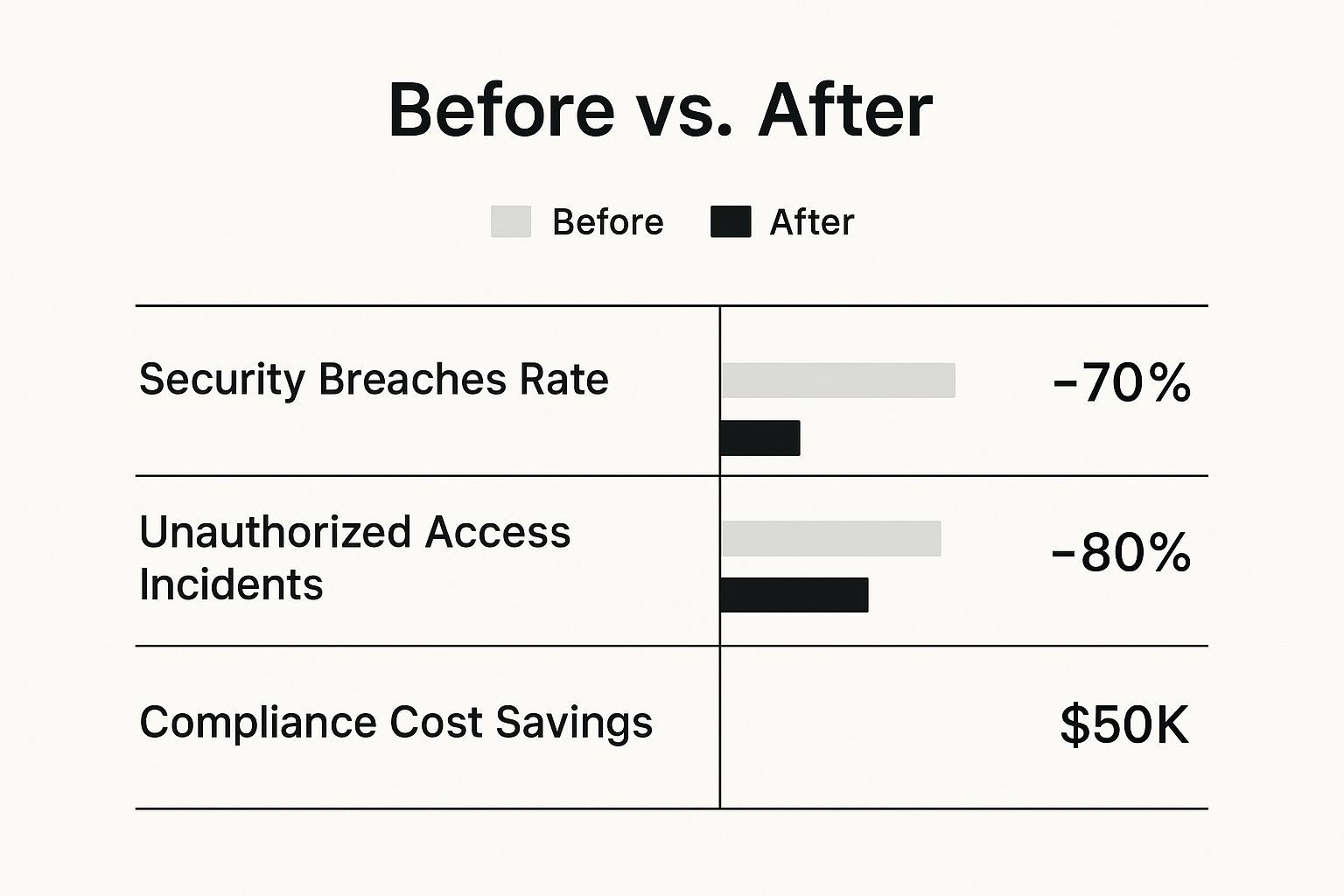
As you can see, getting access control right does more than just stop intruders; it delivers measurable improvements in security and can even reduce operational costs.
The Real-World Benefits of Modern Access Control
Sure, access control is all about security, but its true impact goes way beyond just keeping a door locked. A modern system brings a ton of practical, day-to-day advantages that can make a real difference to your operations, your bottom line, and even your company’s culture.
When you move past the big-picture idea of "better security," you start to see the tangible wins. These systems solve nagging business problems and build a more efficient and accountable workplace for everyone. Let's dig into what that actually looks like.
Streamline Operations and Get Rid of Old Hassles
One of the first things you'll notice is that you can finally say goodbye to the nightmare of managing physical keys. Remember the last time someone left the company and "forgot" to turn in their keys? You had to call a locksmith, pay to have locks re-keyed, and deal with all the disruption just to feel secure again.
With a proper access control system, that entire headache disappears. Instead of calling a locksmith, you just log into the software and revoke that person’s credential. Done. Their access is gone in an instant, saving you time, money, and a whole lot of stress.
This simplicity works just as well when you're bringing people on board.
Easy Onboarding: You can set up a new employee with a key card or mobile pass and give them access to every door they need before their first day.
Simple Temporary Access: Need to let a contractor or visitor in for a few days? You can grant them secure, time-sensitive access that automatically expires when the job is done. No more worrying about unreturned temporary keys.
Boost Accountability with Detailed Audit Trails
Every time someone uses their card or phone to open a door, the system quietly logs it. This creates a powerful digital record of every single event, successful or not. You know who, where, and exactly when.
This audit trail is so much more than a simple log of entries. It’s a game-changer for accountability. Let’s say a server room door was left propped open. Instead of playing a guessing game, you can pull a quick report and see a precise timeline of everyone who entered that room.
This kind of detailed tracking turns your security from a passive fence into an active source of business intelligence. It provides hard data that can settle disputes, expose security weak points, and back up internal investigations.
For any business dealing with compliance regulations, like in healthcare or finance, these audit logs aren't just a nice-to-have. They’re absolutely essential for proving you’re meeting strict security and privacy requirements.
Customize Access for Total Flexibility
A "one-key-fits-all" approach to security just doesn't cut it. Your CEO obviously needs different access than a marketing intern, and the weekend cleaning crew has different needs than your IT team. Access control lets you fine-tune permissions for every single person.
You can create specific access rules based on:
Role: The sales team gets into their office area but not the accounting records room.
Time: Employees might have 24/7 access, but a contractor's credential only works from 9 AM to 5 PM on weekdays.
Location: Someone can get through the main entrance and into the kitchen but is blocked from high-security zones like the data center.
This level of control allows you to implement the principle of least privilege—a cornerstone of modern security. The idea is simple: people should only have access to the places they absolutely need to do their jobs, and nothing more.
This strategy drastically shrinks your risk. If a key card gets lost or stolen, the potential damage is tiny if it only opens a couple of non-critical doors. It’s a smarter, layered way to protect your business.
What's Next for Access Control?
Security isn't what it used to be. We're rapidly moving past the days of clunky hardware and manual gatekeeping, heading toward a future that's more connected, intelligent, and frankly, just easier to live with. This isn't just about bolting on new gadgets; it's a fundamental shift in how we think about and interact with the spaces we occupy.
The next generation of access control is being woven directly into the fabric of our daily routines, becoming smarter, more predictive, and almost invisible.
Your Phone is the New Key
The biggest game-changer? Ditching the on-site server closet for the cloud. For years, access control software was trapped on a dedicated computer, making remote management a nightmare and updates a major project.
Cloud-based systems blow that model wide open. Now, you can manage access for a dozen buildings across the country right from a web browser or an app on your phone. Need to grant a contractor temporary access or revoke a former employee's credentials? It takes seconds, no matter where you are.
This shift pairs perfectly with the rise of mobile access. Let's be honest, we're all carrying a powerful little computer in our pockets. Using your smartphone as a key just makes sense. It’s far more convenient than digging for a key card, and it's often more secure, thanks to built-in protections like Face ID or fingerprint scans.
The future isn't about carrying more plastic cards. It’s about using the secure, powerful devices we already own to create a seamless experience for the right people while keeping the wrong ones out.
Smarter Security That Thinks for Itself
Beyond just opening doors, the next wave of access control is getting a whole lot smarter, thanks to biometrics and artificial intelligence (AI).
Biometrics—using your unique physical traits to prove you are who you say you are—is getting incredibly accurate and reliable. Fingerprint scanners are old news. The new kids on the block are much more sophisticated:
Facial Recognition: Modern systems can identify you in a split second, allowing for truly hands-free, walk-through entry.
Iris and Retina Scans: These offer some of the highest security levels possible, because the patterns in your eyes are virtually impossible to fake.
Behavioral Biometrics: This is where it gets really interesting. Emerging systems can analyze subtle things, like the way you walk, to confirm your identity without you even noticing.
At the same time, Artificial Intelligence (AI) is giving these systems a brain. Instead of just reacting after a breach, an AI-powered system can be proactive. It learns normal patterns and flags anomalies as they happen—like someone trying to access a sensitive area at 3 AM or a secure door being propped open too long—and instantly alerts the right people.
A Market on the Move
This leap in technology is driving massive growth. The global access control market is on track for some serious expansion, projected to jump from USD 19.05 billion in 2025 to over USD 61.31 billion by 2035. That's a compound annual growth rate of 12.4%.
This explosive growth is happening because businesses everywhere are finally trading in their old-school locks for smarter, more flexible digital and biometric solutions. You can dive deeper into the factors driving the access control market's future.
What this all adds up to is a new gold standard for security. It's a system that's not only tougher for intruders to beat but also incredibly simple and intuitive for the rest of us to use every single day.
How to Choose the Right Access Control System
Picking the right access control system can feel like a huge task, but it doesn't have to be. The trick is to step back and ask the right questions before you even look at a single piece of hardware. This isn't just about buying new locks; it's about building a security solution that perfectly fits your space, your budget, and where you see your business heading.
After all, the system that makes sense for a small retail shop is worlds away from what a sprawling corporate headquarters needs.
The best place to start is with a simple walkthrough. Grab a notepad and map out every single entry point in your facility. I'm not just talking about the front door—think about server rooms, executive suites, supply closets, and any other area that needs to be secured. Who needs to get in, and when? This basic map is the foundation for everything else.
Evaluate Your Unique Security Needs
Before you start getting quotes from vendors, you need to get crystal clear on what you're actually protecting. Running through a quick checklist is a great way to nail this down.
Pinpoint Your Vulnerabilities: Where are your most critical assets? This might be a server room packed with sensitive data, a stockroom full of high-value inventory, or an HR office with confidential personnel files.
Define Your User Groups: Not everyone needs the same level of access. Break your people into logical groups: general employees, managers, IT staff, cleaning crews, temporary contractors, and visitors. Each group gets its own set of rules.
Consider Your Traffic Flow: How many people are coming and going each day? A main entrance that sees hundreds of people might need faster, more durable readers to prevent a morning traffic jam.
Doing this homework first is non-negotiable. It keeps you from overspending on flashy features you'll never use or, far worse, leaving your most valuable assets under-protected. For anyone starting this journey, it’s worth understanding the different factors involved in choosing the best access control systems for your home or business.
Plan for Scalability and Future Growth
The system you buy today has to work for the company you'll be tomorrow. It's a classic mistake to pick a solution that fits like a glove right now but has absolutely no room to grow. What happens when you hire more people, open a second office, or need to add more sophisticated security layers? Your system needs to keep up.
Be sure to ask vendors about the system's limits. How many doors can it handle? How many users? Can you manage multiple sites from one dashboard? Modern cloud-based platforms are often the most flexible, letting you scale up without having to rip everything out and start over.
Key Takeaway: Think of this as a long-term investment. The right access control system is more than a security gadget; it's a flexible platform that can adapt as your organization grows and changes.
Finally, look beyond the sticker price. You need to understand the total cost of ownership, which includes the initial installation, any monthly software fees, ongoing maintenance, and the cost of future upgrades. Getting a clear picture of these expenses upfront ensures you won't be hit with nasty surprises later and helps you make a decision that’s truly good for your bottom line.
Frequently Asked Questions
Even after getting the hang of the basics, you probably have a few practical questions about how these systems work in the real world. Let's tackle some of the most common ones to clear up any lingering confusion.
Physical Versus Logical Access Control
So, what's the real difference between physical and logical access control? It’s a great question, and the answer is fundamental to a solid security plan.
Physical access control is exactly what it sounds like—it’s about controlling who can get into physical places. We're talking about doors, server rooms, parking garages, and anything else with a lock on it. It’s the hardware you can see and touch, like keycard readers, biometric scanners, and turnstiles.
On the other hand, logical access control is all about protecting your digital turf. This is what stops unauthorized users from getting into your computer networks, snooping through sensitive files, or accessing proprietary software. It works through passwords, two-factor authentication, and digital permissions. A truly secure business needs both to be locked down tight.
Think of it like a bank. The massive steel vault door is your physical access control. Your online banking password and PIN? That’s logical access control. You wouldn't want one without the other.
System Integration Capabilities
Can you connect an access control system to other security gear? Absolutely. In fact, this is where modern systems really shine. A standalone system is good, but an integrated one acts as the central nervous system for your entire security setup.
For example, you can link your access control system with other platforms to create a powerful, unified defense:
Video Surveillance: Connect your cameras to your door readers. Now, every time someone badges in, the system automatically pulls up video of that event. No more guessing who used a borrowed card.
Alarm Systems: What if a door is forced open or propped open too long? An integrated system can instantly trigger an alarm and notify security, ensuring a rapid response.
HR Software: This one’s a game-changer. When an employee is hired, changes roles, or leaves the company, your HR system can automatically update their access permissions. This closes a huge security gap and saves a ton of administrative time.
Security of Cloud-Based Systems
It’s smart to ask: Are cloud-based access control systems actually secure? It’s a common worry, but the reality is that high-quality cloud platforms are incredibly robust—often even more secure than old-school on-site systems.
Reputable providers host their platforms in professional data centers that have Fort Knox-level physical security and use enterprise-grade encryption to protect your data. Plus, they handle all the security updates and patches for you, so you're never vulnerable because of outdated software. The ability to manage your system from anywhere and get instant alerts on your phone just adds another powerful layer of security.
At PCI Audio-Video Security Solutions, we don't just sell boxes; we design and install advanced access control systems that give you real command over your property. Let's build a solution that fits your business perfectly. Learn more about our customized security options.







Comments